It has been almost two months since I decided to start my studies to get my first certificate into the DEVNET path.
things were really confusing at first because honestly I knew nothing about the programming in general, I studied languages like Pascal in University, but that was longtime ago and lots has changed since then (2005-2009).
Knowing that studying programming in University does not necessarily means you are going to be able to make codes or become a programmer per se.
anyway let us talk about the networking world these days and how Cisco is contributing into making the new network engineering career and keeping it's certified engineers at the top!
As we all know that working on big size networks can be really time consuming sometimes when it comes to routine tasks, things that you might get tasked to do by your manager that require lots of logins and typing lots of commands into switches/routers/firewalls.
and as we all know, many of our networks today are comprised of different products from different vendors.
this impose many risks in addition to the main one which is the time and effort required to do a tasks that might be very simple to achieve on one or two devices but the risk of making mistakes while working on huge network size is high.
this is why, many network engineers who had the programming skills were already trying to solve such problems using programming tools.
we all worked our way using things to make our jobs little bit easier by using Notepad to make scripts for commands and paste them into Network nodes.
this came up handy even in monster exams like CCIE.
in our work environments we might even used SecureCRT and sent commands to all tabs via Command window.
but what if we have hundreds of a mixed products from different companies?
well, Cisco created a whole certification path to help us as engineers to understand and ease our tasks and save our time by learning new but not really new skills that will add up to our knowledge and support us to be more innovative, this is why Cisco DEVNET courses launched to teach us from zero to hero how to be in the new era of Network Engineering.
When Cisco published the free courses on Cisco Learning Network Site, the course had materials that teach you Linux, Windows, MacOS, VSCODE, Python, Git, GitHub and how to make your PC a Development Environment.
https://learningnetwork.cisco.com/s/learning-plan-detail-standard?ltui__urlRecordId=a1c3i0000005hsLAAQ<ui__urlRedirect=learning-plan-detail-standard
You can learn about API and How to practically use Python to make codes that can actually help you in your daily tasks.
All of these mentioned above are standard and can work on any computer free and require nothing to operate.
Of Course the certificate will be joined with a training about Cisco products like Cisco DNA, and Cisco SD-WAN.
Here is a look at the path of the DEVNET certification:
Image soure: Cisco.com
Cisco Has announced the Expert level recently as you can see the "New" above.
This all brings us to the moment where we ask ourselves, do you want to stay as legacy network engineer? or you need to move on and keep yourself updated? of course in IT field, you should always keep your knowledge fresh and up to date, otherwise, you should really think doing something else because IT world is never gonna stop evolving.
you should evolve as well or you are going to extinct.
Ok, so how adding programmability into networking skills going to help me in my work? in simple words, you can make one script that will help you configure or pull data from large number of nodes in few seconds, of course you will keep these codes and use them from time to time whenever needed! what about if they were from different vendors?
that is also ok because you can use libraries in python that can work on different vendors at the same time without the need to create a unique codes for each vendor.
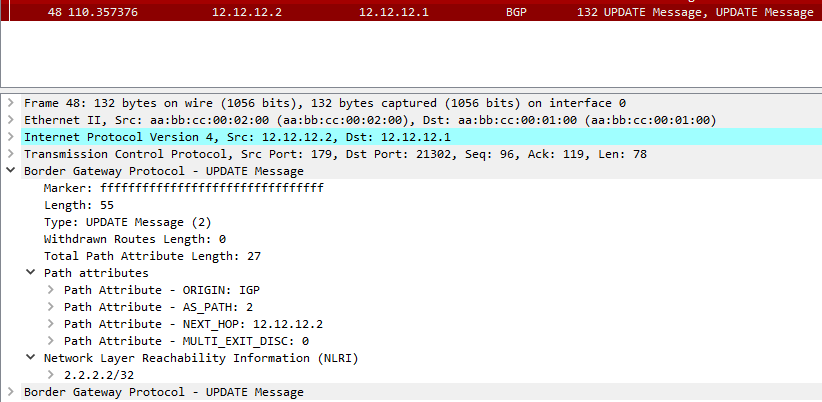
examples: Using NAPALM to configure or get configuration from Nodes, check the list below for the supported vendors.
Image Source:napalm.readthedocs.io
More information about supported list of devices can be found in the link below:
https://napalm.readthedocs.io/en/latest/support/index.html
That being said, How I started my journey into this path? First of course I started with the denial phase, which is "I'm a network engineer and not a programmer!"
which is basically wrong, because network engineers do programming on daily basis while they do their work on any network device!.
anyway, once I had the courage to start, I started with Practical python learning, which is get the code, even if it's copied entirely from a site, I would do it just for the sake of trying a code and see how it works.
My training started with a very cheap course that I got from Udemy for 11$, this course came out handy! I actually used a code to get all serials for a small inventory job which was done in a matter of seconds! (of course making the code work took some work and time to execute :p, but still I can use it in coming tasks and will spend no time to make it work).
Ok, so this was my first course, and the important thing is how you find the Video/Books or blog or anything that will give you the spark to start understand and love the thing that you have been procrastinating to get your hands dirty with!.
every person learns differently, some people like to read books first and some prefer to study by video first. Well, I am the type of video first learners, I like to know what I'm going through before I start, which means I have to watch the videos first and then books.
It does not matter, just do what makes you comfortable and makes study easy.
Another good resource to study for the DEVASC would be the Official certification guide book by Cisco press, if you get the premium edition, it will be joined with a test engine that you can use to test yourself with its question which comes in a multi-choice form.
the book goes through the blueprint and explains the topics in each chapter, you see python and Cisco DNA, API and REST and SD-WAN, JSON and XML YAML and YANG RESTCONF and NETCONF.
The crucial part of preparing your development environment is choosing the system you will work on, is it gonna be Linux or windows or MacOS? I have seen many people recommending Linux Ubuntu, and Cisco video courses does go through the setup of Ubuntu as a workstation for such a thing, but I chose Windows and MacOS.
basically MacOS is the most programming friendly environment IMO.
so why go to Ubuntu? of course it does not hurt to learn linux but in my case I want to most stable system.
next, you will need to decide how you will practice and run your codes? because you can use VSCODE to make codes and send to a real/lab nodes directly, but also GNS3 is great option to do your labs, especially the option to download network automation appliance that comes with all needed tools ready to use. (you can search it and find it on GNS3 site).
personally I prefer both, GNS3 and real equipment because once you make sure your script is fine, you can make some use of it.
there is a list of requirements that you need to make sure to download and install on your environment whether it was linux or windows or MacOS.
the list is but not limited to: Python (latest version)
Ansible, Paramiko (netmiko), telnet library, NAPALM, PyATS, YANG, JSON....etc.
Note that with all the pros of network programmability there is of course cons, because we cannot exclude the human error factor from this, imagine running a code for a number of devices with some mistake in the code, this is going to be catastrophic to some environments.
This is my journey toward Cisco DEVASC, it started and not going to end until I achieve my goal and pass the exam.
Will be updated soon!
Samer R. Saleem