In today's post, we will work on creating an Access Control List that works in specific time that we decide, this could be useful for a cases that you want to filter traffic according to that time you set
In many cases you can use this time based ACL, so let's create a simple lab showing the use of it.
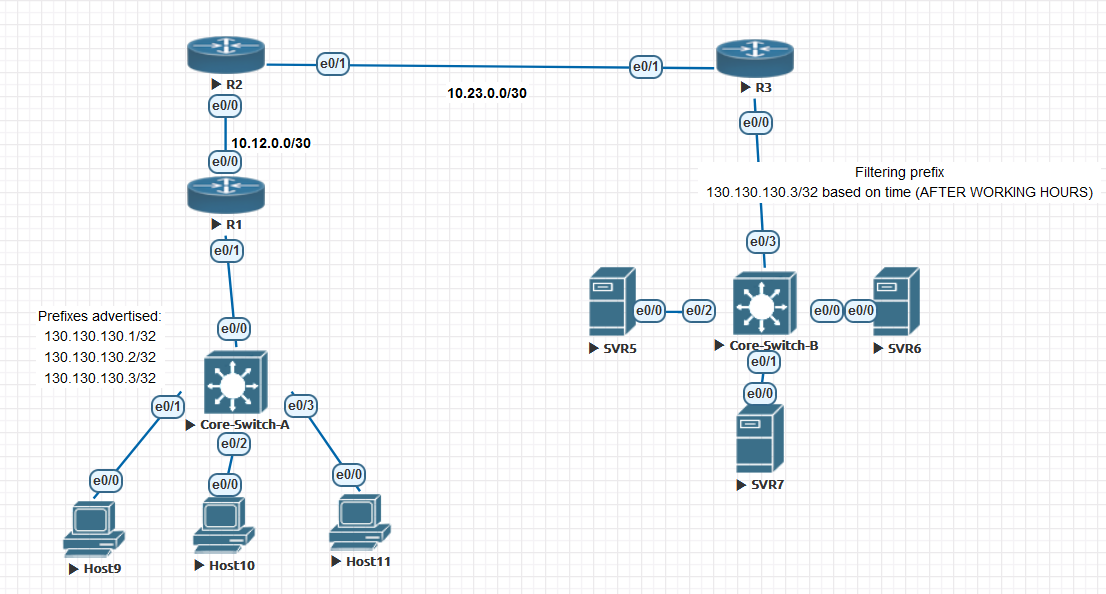
First, as usual we will use a simple topology because there is no need to make thing complicated, all you need is three routers or layer3 switches
In my lab, I will be using three Cisco Routers with 15.4T IOS version.
Topology below:
In the topology above, R1 hosts 9, 10, 11 will be advertised as a loopback prefixes from R1.
we will filter the access for these hosts inbound to Site-B on R3 to stop unwanted traffic after working hours to SVR5, SVR6, SVR7
in my example, I will filter only one of the IP's for the sake of explanation to make sure the rest of hosts have reachability after the filtration.
After configuring EIGRP between the three sites, we can see the routing tables with prefixes for the advertised networks
on both sides.
As you can see above, the host that we will filter is 130.130.130.3/32, we will configure any time that we like the policy
to start working in it, then we will monitor our logs.
remember it is better to enable logs with the Access list that we will configure in order to see the hits on the policy for the matching
packets.
Note: the Time based ACL will only be in extended Access Control lists and not in standard.
Now, it is time to define the time range that will be used in access list.
Commands are:
time-range AFTER-WORK
absolute start 08:25 26 June 2021
absolute end 08:43 26 june 2021
the Access list configured as below:
#ip access-list extended TIME
#deny ip host 130.130.130.3 any time-range AFTER-WORK log
#permit ip any any time-range TIME log
apply it inboung on E0/1 or Router3 and check if its active:
here you go, we have hits on both lines, where we generated some ICMP packets sourced from 130.130.130.3/32
and the permitted log matches the other traffic which include EIGRP packets as well.
As you can see, the packets not reaching the 5.5.5.5/32 SVR when the source of the ICMP is 130.130.130.3/32
Here above you can see the logs generated by the hit on R3 for both the denied logs and permitted EIGRP packets.
Note: before the time range is activated, it should be seen as inactive as below:
Ok, please note that you must put end option to the time-range settings:
#time-range AFTER-WORK
#absolute end 08:42 26 June 2021
which will put the ACL back to inactive state.
Ok, what about making this task automated? the answer is also by using time-range but with another option which is:
That was it, I hope you enjoyed this post!
Samer Rafid Saleem