Here is a lab to configure Site to Site VPN, this is a great service to help companies to connect their branches and of course it is important when companies start to expand.
as a network engineer, you are required to provide the needed network and security infrastructure to help your organization to achieve its goals and help business continuity.
so let's go through the configuration between two sites, and remember this is a lab environment, real life scenarios could be different in some cases.
you might think this topology is very simple, but this is all you need to do your lab!
So why not!
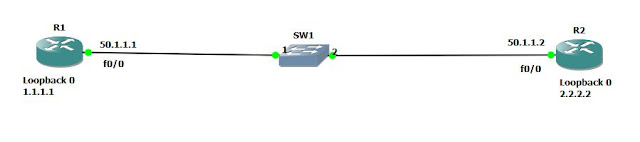
IPsec Site-to-Site VPN between Router #1 and Router #2
R1 IP is 50.1.1.1 with Loopback 0 IP of 1.1.1.1
R2 IP is 50.1.1.2 with Loopback 0 IP of 2.2.2.2
We will establish the VPN be between the Loopback interfaces (to be considered LAN interfaces traffic of two the companies).
So in this LAB the traffic between the two LAN's will be going under the process of Encryption and Decryption
the peering will be done on the two Public IP's
R1 Configs:
archive
log config
hidekeys
crypto isakmp policy 10
encr aes
authentication pre-share
group 5
crypto isakmp key 6 cisco address 50.1.1.2
crypto ipsec transform-set ts esp-aes esp-sha-hmac
crypto map cmap 10 ipsec-isakmp
set peer 50.1.1.2
set transform-set ts
match address vpn
ip tcp synwait-time 5
interface Loopback0
ip address 1.1.1.1 255.255.255.0
interface FastEthernet0/0
ip address 50.1.1.1 255.255.255.0
duplex auto
speed auto
crypto map cmap
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 50.1.1.2
no ip http server
no ip http secure-server
!
ip access-list extended vpn
permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
R2 Config:
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 5
crypto isakmp key 6 cisco address 50.1.1.1
!
!
crypto ipsec transform-set ts esp-aes esp-sha-hmac
!
crypto map cmap 10 ipsec-isakmp
set peer 50.1.1.1
set transform-set ts
match address vpn
!
!
!
ip tcp synwait-time 5
!
!
!
!
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
interface FastEthernet0/0
ip address 50.1.1.2 255.255.255.0
duplex auto
speed auto
crypto map cmap
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 50.1.1.1
!
!
no ip http server
no ip http secure-server
!
ip access-list extended vpn
permit ip 2.2.2.0 0.0.0.255 1.1.1.0 0.0.0.255
!
Verify:
lets verify that we have everything OK on ISAKMP
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
50.1.1.2 50.1.1.1 QM_IDLE 1001 0 ACTIVE
Note: you need to send traffic between both peers in order to make the session up.
verify IPSEC
sending traffic from the source of Lo0 to destination of Lo0 which will match the ACL configuration for the traffic to be protected will give the below result.
R1#ping 2.2.2.2 source loopback 0 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
......!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 94 percent (94/100), round-trip min/avg/max = 4/14/48 ms
R1#show crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: cmap, local addr 50.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (2.2.2.0/255.255.255.0/0/0)
current_peer 50.1.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 94, #pkts encrypt: 94, #pkts digest: 94
#pkts decaps: 94, #pkts decrypt: 94, #pkts verify: 94
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 6, #recv errors 0
local crypto endpt.: 50.1.1.1, remote crypto endpt.: 50.1.1.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0xAD55A003(2908069891)
inbound esp sas:
spi: 0x4052EA88(1079175816)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, crypto map: cmap
sa timing: remaining key lifetime (k/sec): (4429861/3489)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAD55A003(2908069891)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, crypto map: cmap
sa timing: remaining key lifetime (k/sec): (4429861/3489)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R1#
on R2 the SPI should be the same sent from R1 but the outbound would be inbound and vice versa
check below output:
inbound esp sas:
spi: 0xAD55A003(2908069891)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, crypto map: cmap
sa timing: remaining key lifetime (k/sec): (4521941/3279)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x4052EA88(1079175816)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, crypto map: cmap
sa timing: remaining key lifetime (k/sec): (4521941/3279)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 5
crypto isakmp key 6 cisco address 50.1.1.1
!
!
crypto ipsec transform-set ts esp-aes esp-sha-hmac
!
crypto map cmap 10 ipsec-isakmp
set peer 50.1.1.1
set transform-set ts
match address vpn
!
!
!
ip tcp synwait-time 5
!
!
!
!
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
interface FastEthernet0/0
ip address 50.1.1.2 255.255.255.0
duplex auto
speed auto
crypto map cmap
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 50.1.1.1
!
!
no ip http server
no ip http secure-server
!
ip access-list extended vpn
permit ip 2.2.2.0 0.0.0.255 1.1.1.0 0.0.0.255
!
Verify:
lets verify that we have everything OK on ISAKMP
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
50.1.1.2 50.1.1.1 QM_IDLE 1001 0 ACTIVE
Note: you need to send traffic between both peers in order to make the session up.
verify IPSEC
sending traffic from the source of Lo0 to destination of Lo0 which will match the ACL configuration for the traffic to be protected will give the below result.
R1#ping 2.2.2.2 source loopback 0 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
......!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 94 percent (94/100), round-trip min/avg/max = 4/14/48 ms
R1#show crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: cmap, local addr 50.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (2.2.2.0/255.255.255.0/0/0)
current_peer 50.1.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 94, #pkts encrypt: 94, #pkts digest: 94
#pkts decaps: 94, #pkts decrypt: 94, #pkts verify: 94
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 6, #recv errors 0
local crypto endpt.: 50.1.1.1, remote crypto endpt.: 50.1.1.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0xAD55A003(2908069891)
inbound esp sas:
spi: 0x4052EA88(1079175816)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, crypto map: cmap
sa timing: remaining key lifetime (k/sec): (4429861/3489)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAD55A003(2908069891)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, crypto map: cmap
sa timing: remaining key lifetime (k/sec): (4429861/3489)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R1#
on R2 the SPI should be the same sent from R1 but the outbound would be inbound and vice versa
check below output:
inbound esp sas:
spi: 0xAD55A003(2908069891)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, crypto map: cmap
sa timing: remaining key lifetime (k/sec): (4521941/3279)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x4052EA88(1079175816)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, crypto map: cmap
sa timing: remaining key lifetime (k/sec): (4521941/3279)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
Samer R. Saleem



No comments:
Post a Comment