SSL Decryption is a feature that is used by the Firewalls and web gateways to inspect encrypted traffic such as HTTPS, the SSL decryption will make the firewall work as a proxying the user for the traffic to remote destinations and requests.
NOTE: SSL Scan/inspection can cause high impact on the Firewall resources and might cause network interruption if misconfigure.
With that been said, Firewall will for sure need to create two sessions
1. From user to firewall
2. From firewall to remote site
So, the firewall must have a certificate created in order to be installed on the user computer or Mobile device, to do that you will need to do the following:
Device > Certificate Management > certificates > Generate
the IP should be the inside interface IP address of the firewall.
Now this certificate will not be used until we implement the decryption policy.
To create the decryption policy we will:
Go to > Policies > Decryption > Add
Add the name, source zone and IP address, destination and then the action to decrypt the traffic matching source address.
Now that we have created the policy, the IP matched in it will not be able to go www.youtube.com unless the certificate created by the Firewall is installed, and below message will be seen once the firewall start inspecting the traffic, if you select “NO” then the traffic will not pass and will be dropped.
Ok, How to install the certificate on the computer or mobile?
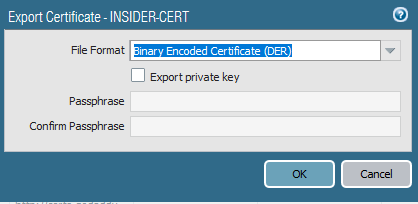
What I have done is exporting the certificate I generated at the beginning, saved locally on my computer, and then imported it on the computer as trusted certificate.
Go to Device > Certificate management > certificates.
Select the certificate and then export .der file and then install this file on the device you need to make SSL inspection on.








No comments:
Post a Comment